Easily improve site security with WordPress Hardening, Two-Factor Authentication (2FA), Login Protection, Vulnerability Detection and SSL certificate.
Headers Security Advanced & HSTS WP
Hospedagem WordPress com plugin Headers Security Advanced & HSTS WP
Onde hospedar o plugin Headers Security Advanced & HSTS WP?
Este plugin pode ser hospedado em qualquer servidor que possua WordPress instalado. Recomendamos escolher um provedor de hospedagem confiável, com servidores especializados para WordPress, como o serviço de hospedagem da MCO2.
Hospedando o plugin Headers Security Advanced & HSTS WP em um provedor seguro
A MCO2, além de instalar o WordPress na versão mais atualizada para seus clientes, fornece o plugin WP SafePress, um sistema singular que salvaguarda e melhora seu site simultaneamente.
Por que a Hospedagem WordPress funciona melhor na MCO2?
A Hospedagem WordPress funciona melhor pois a MCO2 possui servidores otimizados para WordPress. A instalação de WordPress é diferente de uma instalação trivial, pois habilita imediatamente recursos como otimização automática de imagens, proteção da página de login, bloqueio de atividades maliciosas diretamente no firewall, cache avançado e HTTPS ativado por padrão. São plugins que potencializam seu WordPress para a máxima segurança e o máximo desempenho.
Headers Security Advanced & HSTS WP is Best all-in-one a free plug-in for all WordPress users. Deactivating this plugin will return your site configuration exactly to the state it was in before.
The Headers Security Advanced & HSTS WP project implements HTTP response headers that your site can use to increase the security of your website. The plug-in will automatically set up all Best Practices (you don’t have to think about anything), these HTTP response headers can prevent modern browsers from running into easily predictable vulnerabilities. The Headers Security Advanced & HSTS WP project wants to popularize and increase awareness and usage of these headers for all wordpress users.
This plugin is developed by TentaclePlugins by irn3, we care about WordPress security and best practices.
Check out the best features of Headers Security Advanced & HSTS WP:
- X-XSS-Protection (Deprecated)
- Pragma (Deprecated)
- Public-Key-Pins (Deprecated)
- Expect-CT (Deprecated)
- Access-Control-Allow-Origin
- Access-Control-Allow-Methods
- Access-Control-Allow-Headers
- X-Content-Security-Policy
- X-Content-Type-Options
- X-Frame-Options
- X-Permitted-Cross-Domain-Policies
- X-Powered-By
- Content-Security-Policy
- Referrer-Policy
- HTTP Strict Transport Security / HSTS
- Content-Security-Policy
- Content-Security-Policy-Report-Only
- Clear-Site-Data
- Cross-Origin-Embedder-Policy-Report-Only
- Cross-Origin-Opener-Policy-Report-Only
- Cross-Origin-Embedder-Policy
- Cross-Origin-Opener-Policy
- Cross-Origin-Resource-Policy
- Permissions-Policy
- Strict-dynamic
- Strict-Transport-Security
- FLoC (Federated Learning of Cohorts)
Headers Security Advanced & HSTS WP is based on OWASP CSRF to protect your wordpress site. Using OWASP CSRF, once the plugin is installed, it will provide full CSRF mitigation without having to call a method to use nonce on the output. The site will be secure despite having other vulnerable plugins (CSRF).
HTTP security headers are a critical part of your website’s security. After automatic implementation with Headers Security Advanced & HSTS WP, they protect you from the most notorious types of attacks your site might encounter. These headers protect against XSS, code injection, clickjacking, etc.
We have put a lot of effort into making the most important services operational with Content Security Policy (CSP), below are some examples that we have tested and used with Headers Security Advanced & HSTS WP:
- CSP usage for Google Tag Manager
world’s most popular tag manager - Using CSP for Gravatar
Avatar service for WordPress and Social sites - Using CSP for WordPress Internal Media
support WordPress media - Using CSP for Youtube Embedded Video SDK
support Youtube embedded frames and JS SDK - CSP usage for CookieLaw
privacy technology to meet regulatory requirements - CSP usage for Mailchimp
support for Mailchimp automation, SDK and modules - CSP usage for Google Analytics
support for basic conversion domains such as: stats.g.doubleclick.net and www.google.com - CSP usage for Google Fonts
you’re not loading it on the page, chances are one of your SDKs is using it - Using CSP for Facebook
support Facebook SDK functionality - Using CSP for Stripe
highly secure online payment system - Using CSP for New Relic
it’s a registration and monitoring utility - Using CSP for Linkedin Tags + SDKs
support Linkedin Insight, Linkedin Ads and SDK - Using CSP for OneTrust
OneTrust support helps companies manage privacy requirements - CSP usage for Moat
Moat support to measurement suite such as: ad verification, brand safety, advertising and coverage - CSP usage for jQuery
support of jQuery – JS library - CSP usage for Twitter Widgets & SDKs
support Connect, Widgets and the Twitter client-side SDK - Using CSP for Google Maps
support Google Maps as The ggpht used by streetview - Using CSP for Quantcast Choice
Quantcast support for privacy such as GDPR and CCPA - CSP usage for Twitter Ads & Analytics
Twitter support for advertising and Analytics - Using CSP for Paypal
PayPal support for online payment system - Using CSP for Drift
Drift and Driftt support - CSP usage for Cookiebot
cookie and tracker support, GDPR/ePrivacy and CCPA compliance - CSP usage for Vimeo Embedded Videos SDK
support frames, JS SDK, Froogaloop integration - Using CSP for AppNexus (now Xandr)
AppNexus support for custom retargeting - Using CSP for Mixpanel
support analytics tool with SDK/JS to collect client-side data - Using CSP for Font Awesome
toolkit support for fonts and icons over CSS and Less - Using CSP for Google reCAPTCHA
reCAPTCHA support for fraud and bot protection - CSP usage for Bootstrap CDN
Bootstrap support for CSS frameworks - Using CSP for HubSpot
Hubspot support with many features, used for monitoring and mkt functionality - Using CSP for Hotjar
Hotjar tracker support for analytics and metrics - Using CSP for WP.com
support for wp.com hosting - Using CSP for Akamai mPulse
support for Akamai mPulse, for origin and perimeter integrations - CSP usage for Cloudflare – Rocket-Loader & Mirage
support for Mirage libraries for performance acceleration - Using CSP for Cloudflare – CDN.js
Cloudflare’s open CDN support with multiple libraries - Using CSP for jsDelivr
support jsDelivr free CDN for Open Source
Headers Security Advanced & HSTS WP is based on the OWASP CSRF standard to protect your wordpress site. Using the OWASP CSRF standard, once the plugin is installed, you can customize CSP rules for full CSRF mitigation. The site will be secure despite having other vulnerable plugins (CSRF).
Integration with Sentry, Report URI, URIports and Datadog
Sentry is a well-known platform for monitoring and tracking errors in applications. By integrating Sentry with our plugin, users can:
* Receive detailed reports on content security policy (CSP) violations.
* Monitor and analyze JavaScript exceptions occurring on their site.
* Benefit from advanced tools for proactive troubleshooting.
Monitoring and Integration with Sentry, Datadog and URI Reports for optimal security.
All Free Features
The Headers Security Advanced & HSTS WP version includes all the free features.
We have implemented FLoC (Federated Learning of Cohorts), using best practices. First, using Headers Security Advanced & HSTS WP prevents the browser from including your site in the “cohort calculation” on FLoC (Federated Learning of Cohorts). This means that nothing can call document.interestCohort() to get the FLoC ID of the currently used client. Obviously, this does nothing outside of your currently visited site and does not “disable” FLoC on the client beyond that scope.
Even though FLoC is still fairly new and not yet widely supported, as programmers we think that privacy protection elements are important, so we choose to give you the feature of being opt out of FLoC! We’ve created a special “automatic blocking of FLoC” feature, trying to always offer the best tool with privacy protection and cyber security as main targets and focus.
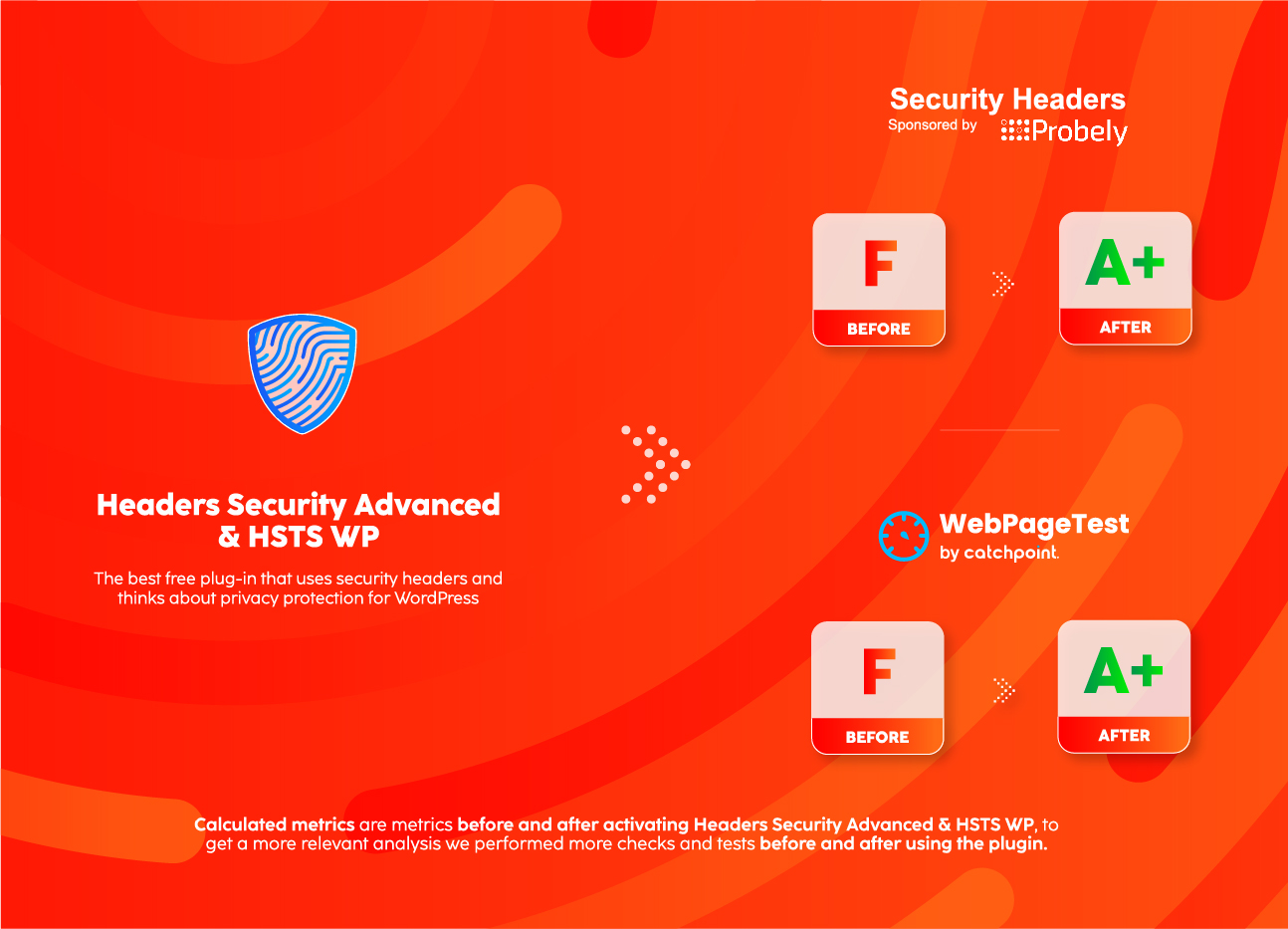
Analyze your site before and after using Headers Security Advanced & HSTS WP security headers are self-configured according to HTTP Security Headers and HTTP Strict Transport Security / HSTS best practices.
- Check HTTP Security Headers on securityheaders.com
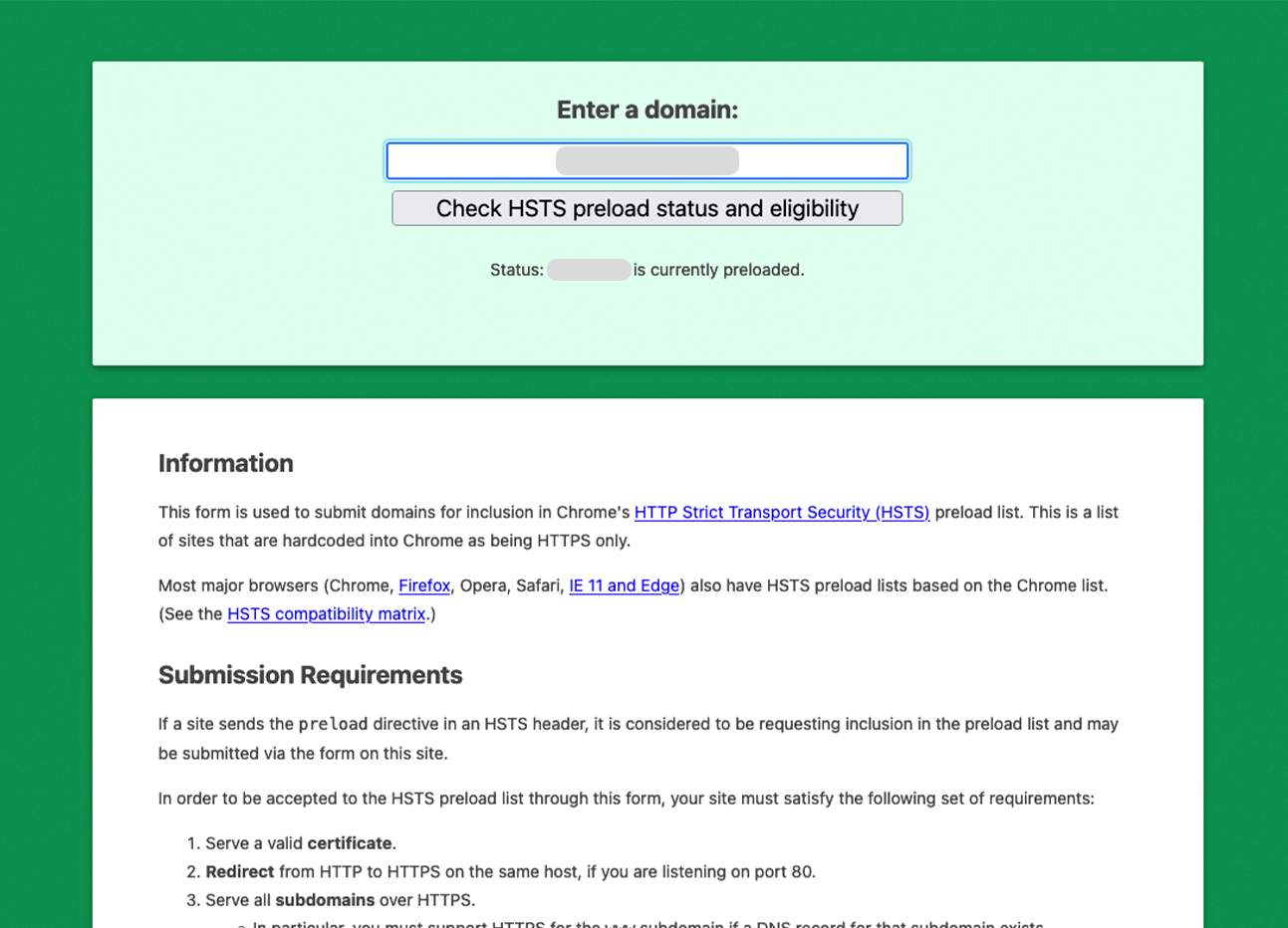
- Check HTTP Strict Transport Security / HSTS at hstspreload.org
- Check WebPageTest at webpagetest.org
- Check HSTS test website gf.dev/hsts-test
- Check CSP test website csper.io/evaluator
- Check CSP Evaluator csp-evaluator.withgoogle.com
- CSP Content Security Policy Generator addons.mozilla.org
This plugin is updated periodically, our limited support is free, we are available for your feedback (bugs, compatibility issues or recommendations for next updates). We are usually fast :-D.
Capturas de tela
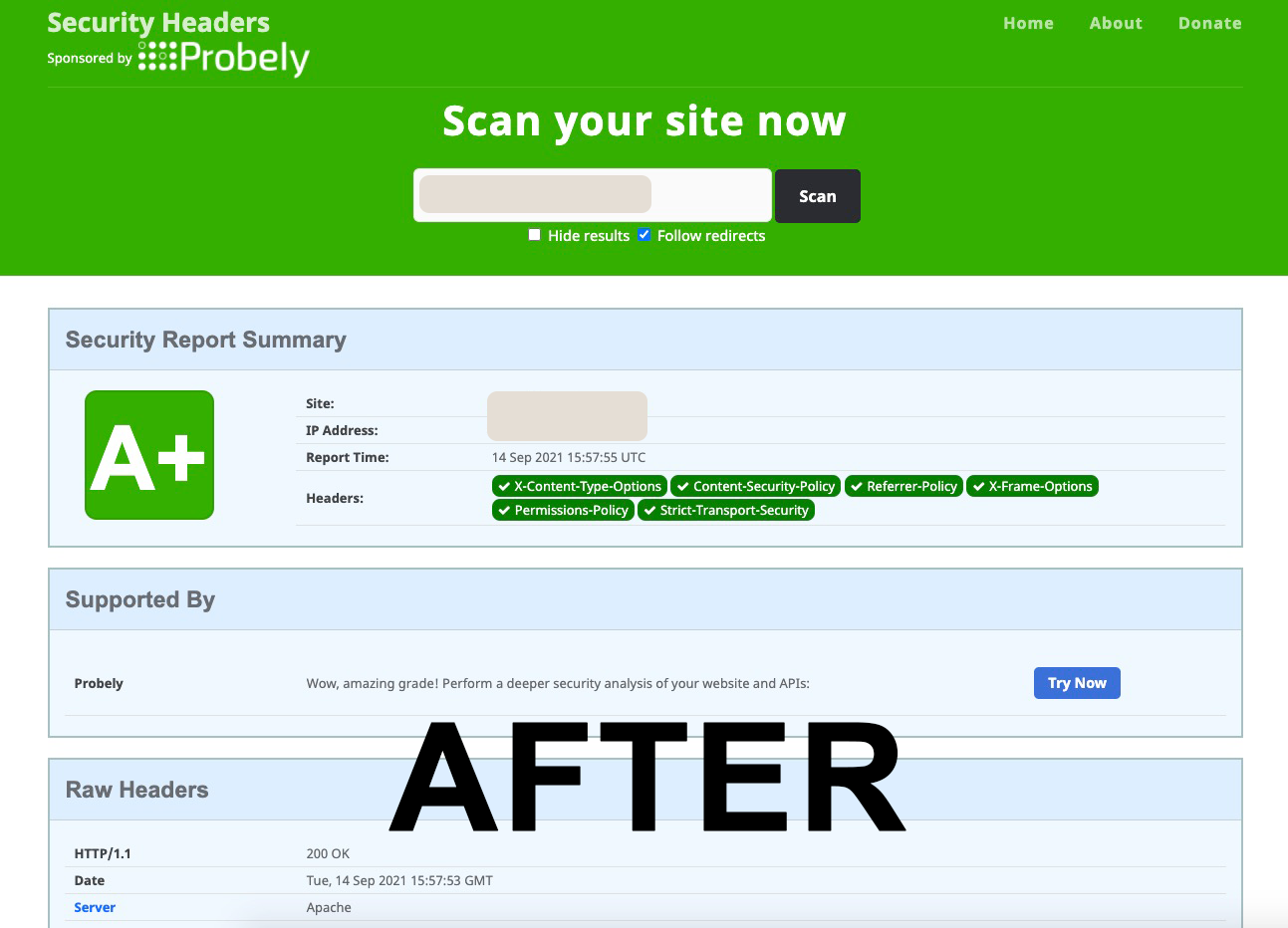
Check HTTP Security Headers (AFTER)
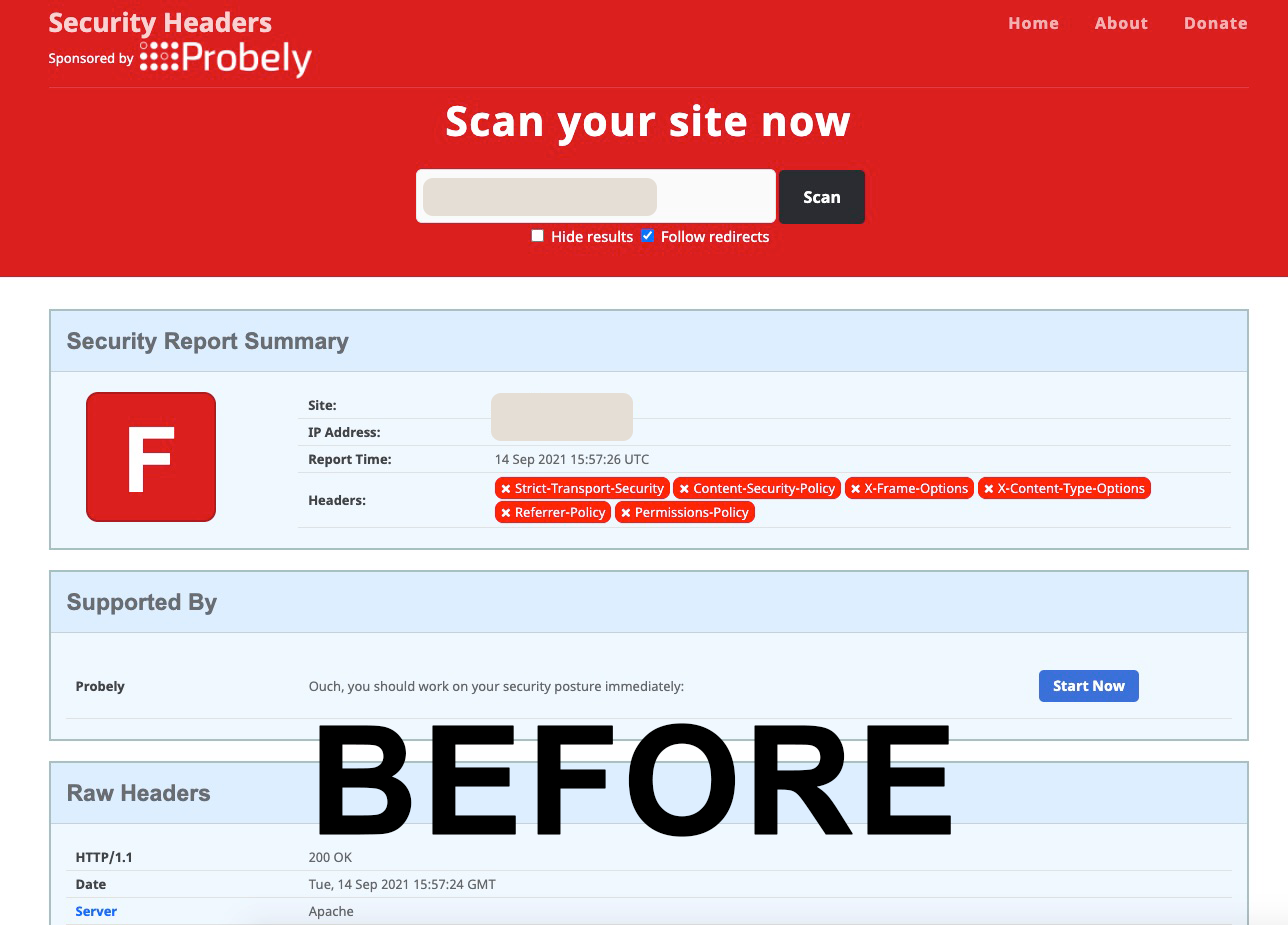
Check HTTP Security Headers (BEFORE)
Check HTTP Strict Transport Security / HSTS (list)
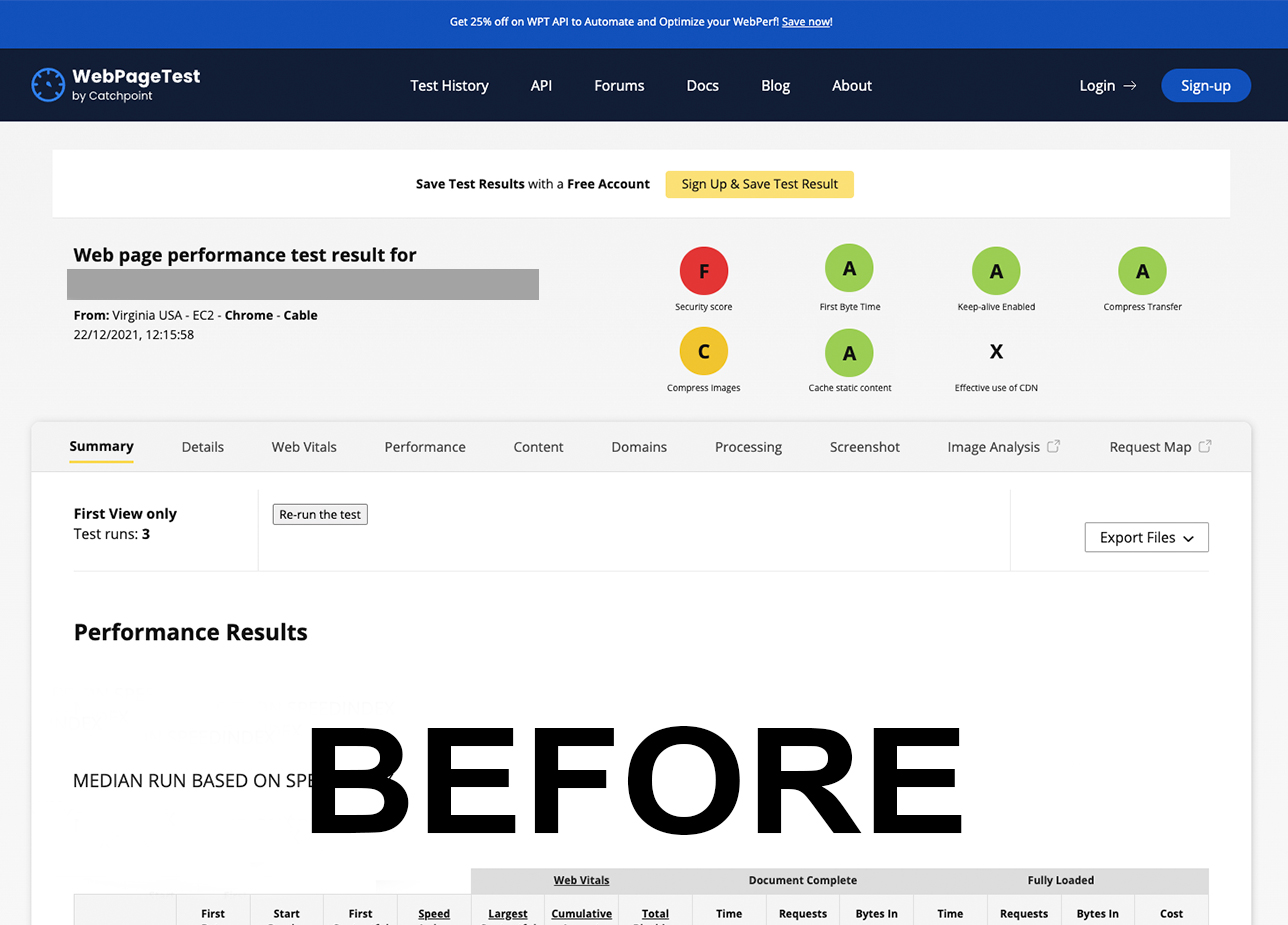
Check WebPageTest (AFTER)
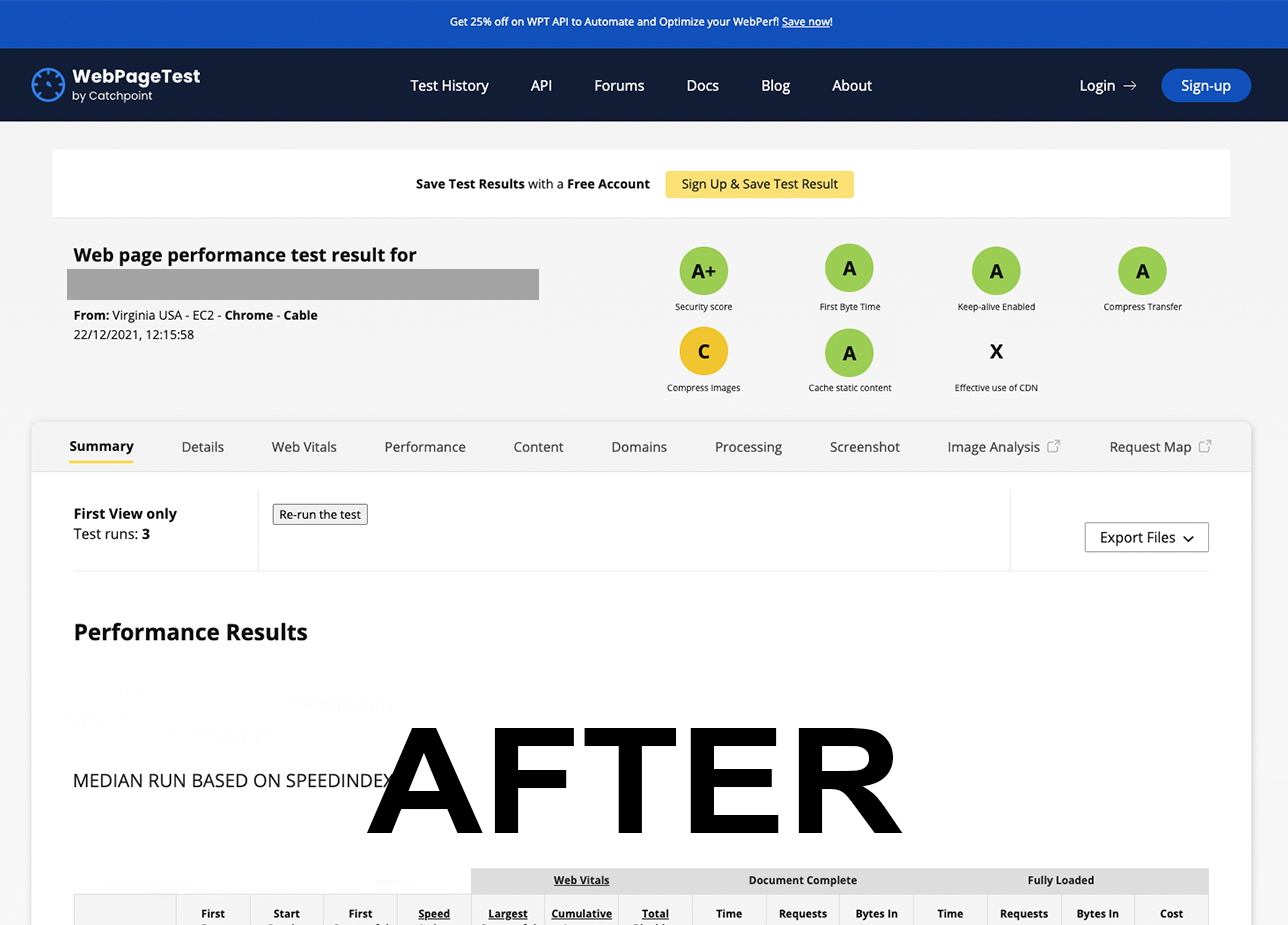
Check WebPageTest (BEFORE)
Setting on single site installation
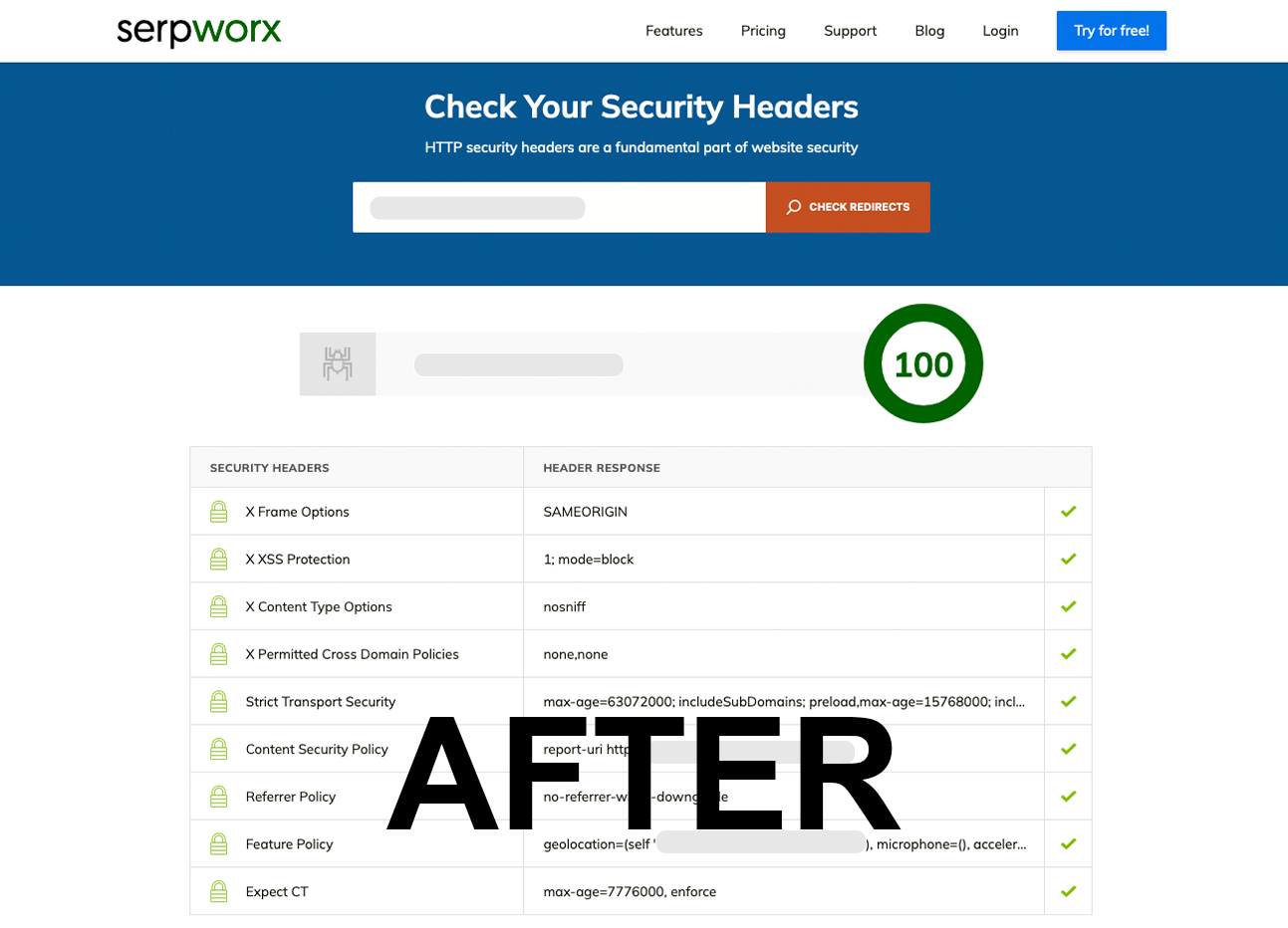
Check HTTP Security Headers - Serpworx (AFTER)
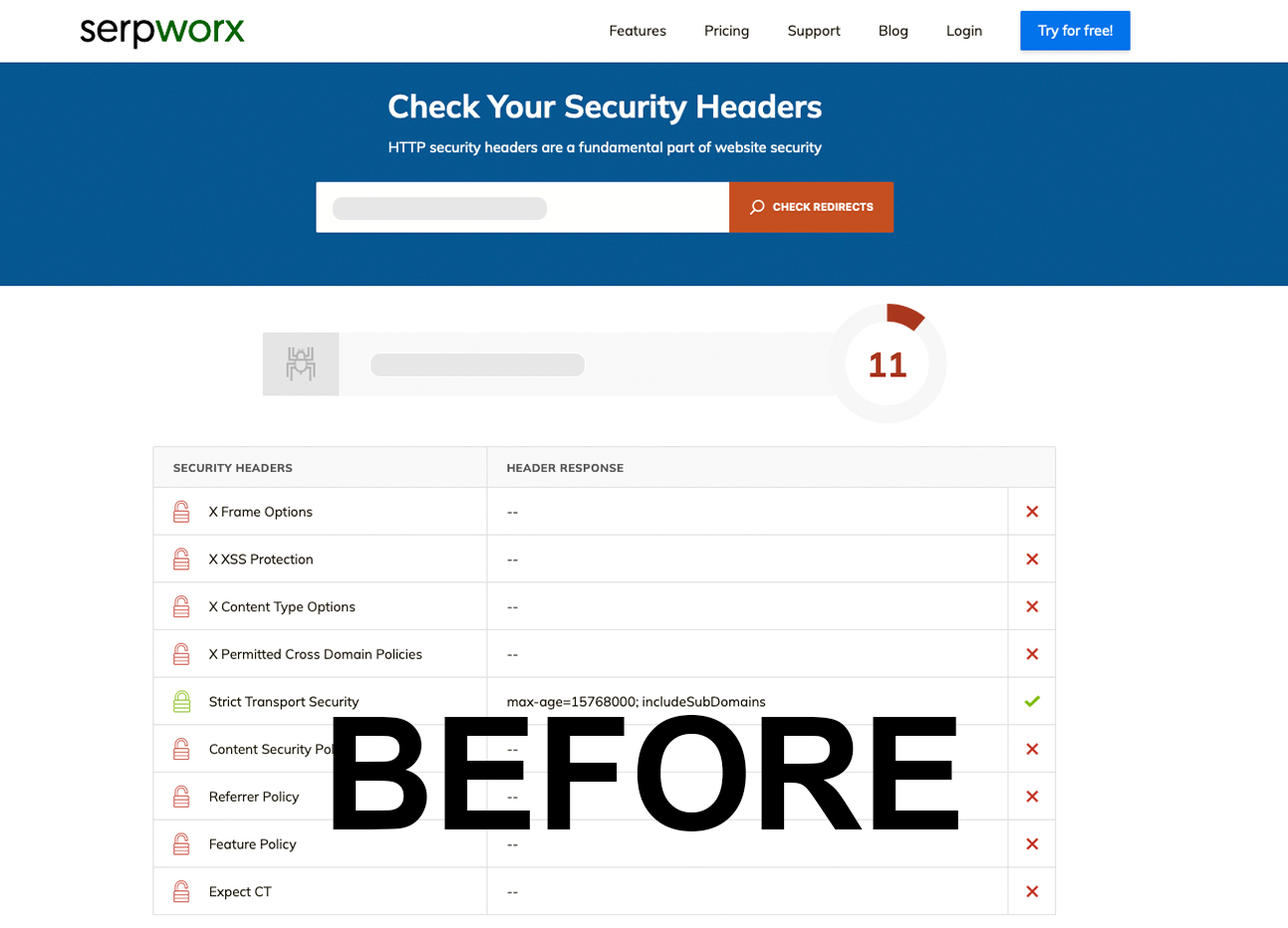
Check HTTP Security Headers - Serpworx (BEFORE)
Site-wide security setting
