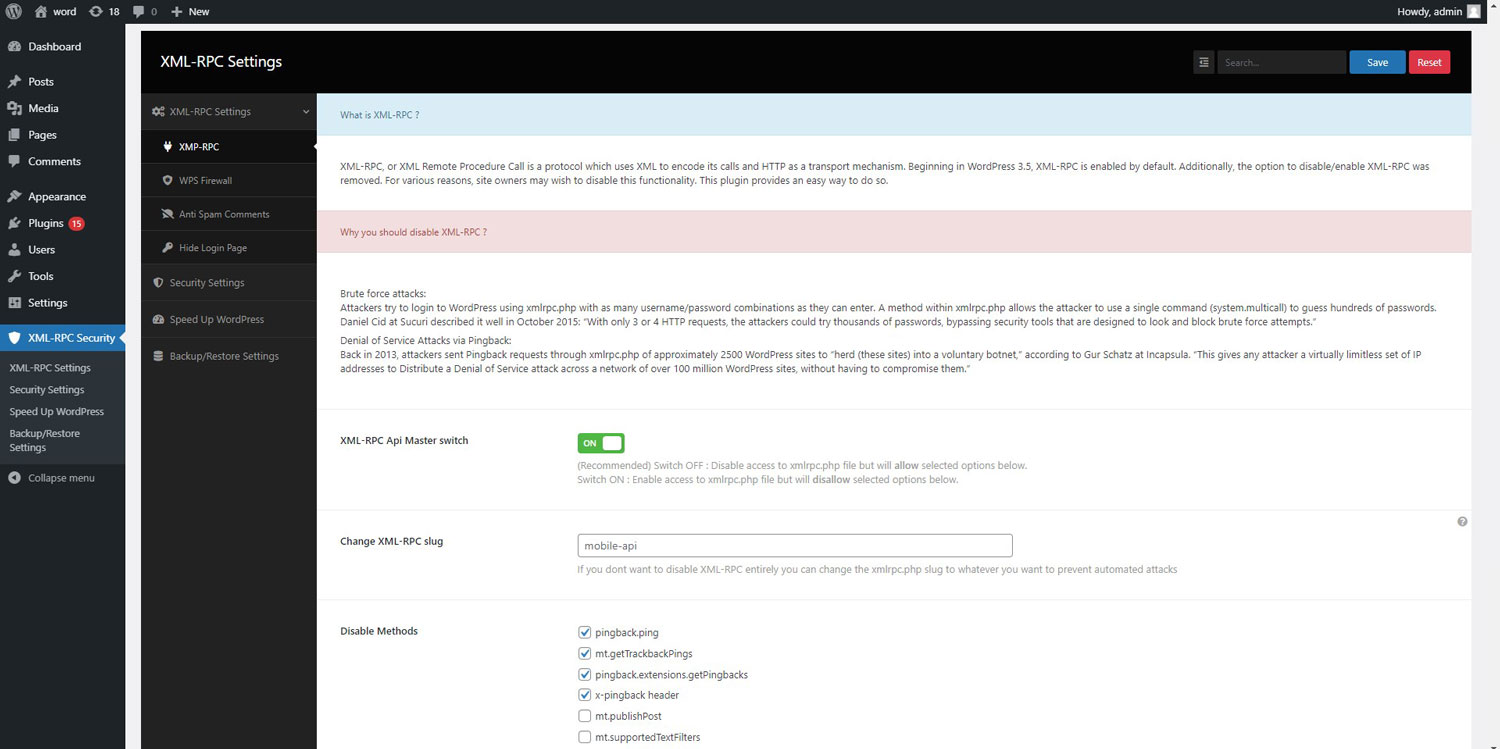
Disables the XML-RPC API in WordPress 3.5+, which is enabled by default.
Disable XML-RPC-API
Hospedagem WordPress com plugin Disable XML-RPC-API
Onde devo hospedar o plugin Disable XML-RPC-API?
Este plugin pode ser hospedado em qualquer provedor que possua WordPress instalado. Recomendamos utilizar uma empresa de hospedagem de confiança, com servidores adaptados para WordPress, como o serviço de hospedagem de sites da MCO2.
Hospedando o plugin Disable XML-RPC-API em um provedor confiável
A MCO2, além de instalar o WordPress na versão mais nova para seus clientes, disponibiliza o plugin WP SafePress, um mecanismo exclusivo que salvaguarda e aumenta a performance do seu site ao mesmo tempo.
Por que a Hospedagem WordPress funciona melhor na MCO2?
A Hospedagem WordPress funciona melhor pois a MCO2 possui servidores otimizados para WordPress. A instalação de WordPress é diferente de uma instalação trivial, pois habilita imediatamente recursos como otimização de imagens, proteção da página de login, bloqueio de atividades suspeitas diretamente no firewall, cache avançado e HTTPS ativado por padrão. São plugins que potencializam seu WordPress para a máxima segurança e o máximo desempenho.
Protect your website from xmlrpc brute-force attacks,DOS and DDOS attacks, this plugin disables the XML-RPC and trackbacks-pingbacks on your WordPress website.
PLUGIN FEATURES
(These are options you can enable or disable each one)
- Disable access to xmlrpc.php file using .httacess file
- Automatically change htaccess file permission to read-only (0444)
- Disable X-pingback to minimize CPU usage
- Disable selected methods from XML-RPC
- Remove pingback-ping link from header
- Disable trackbacks and pingbacks to avoid spammers and hackers
- Rename XML-RPC slug to whatever you want
- Black list IPs for XML-RPC
- White list IPs for XML-RPC
- Some options to speed-up your wordpress website
- Disable JSON REST API
- Hide WordPress Version
- Disable built-in WordPress file editor
- Disable wlw manifest
- And some other options
What is XMLRPC
XML-RPC, or XML Remote Procedure Call is a protocol which uses XML to encode its calls and HTTP as a transport mechanism.
Beginning in WordPress 3.5, XML-RPC is enabled by default. Additionally, the option to disable/enable XML-RPC was removed. For various reasons, site owners may wish to disable this functionality. This plugin provides an easy way to do so.
Why you should disable XML-RPC
Xmlrpc has two main weaknesses
- Brute force attacks:
Attackers try to login to WordPress using xmlrpc.php with as many username/password combinations as they can enter. A method within xmlrpc.php allows the attacker to use a single command (system.multicall) to guess hundreds of passwords. Daniel Cid at Sucuri described it well in October 2015: “With only 3 or 4 HTTP requests, the attackers could try thousands of passwords, bypassing security tools that are designed to look and block brute force attempts.” - Denial of Service Attacks via Pingback:
Back in 2013, attackers sent Pingback requests through xmlrpc.php of approximately 2500 WordPress sites to “herd (these sites) into a voluntary botnet,” according to Gur Schatz at Incapsula. “This gives any attacker a virtually limitless set of IP addresses to Distribute a Denial of Service attack across a network of over 100 million WordPress sites, without having to compromise them.”
Capturas de tela